Dynamic Tools
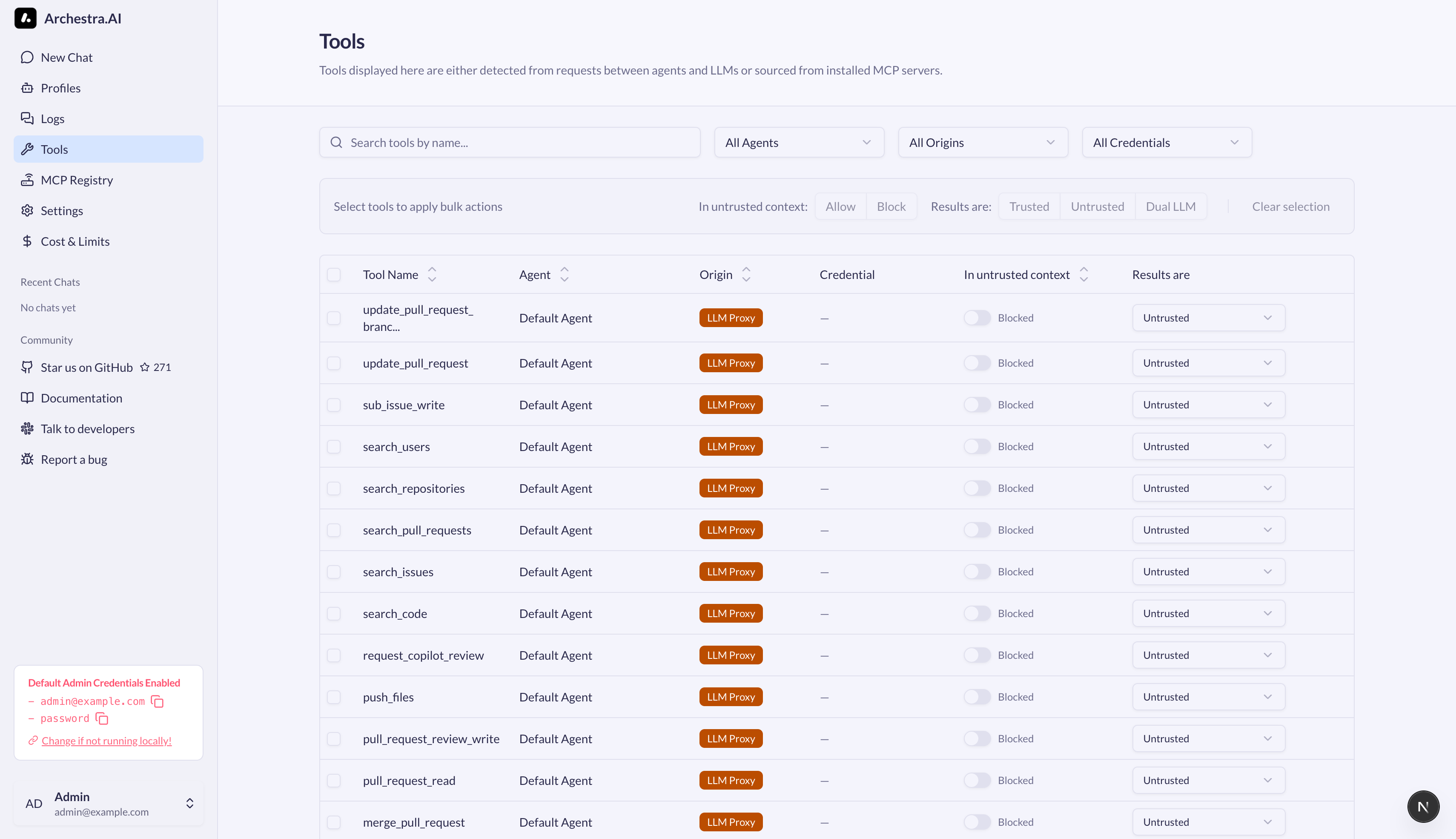
Dynamic Tools feature af the Archestra Platform addresses the "lethal trifecta" by adapting agent capabilities based on trust levels, providing more flexibility than read-only or isolated systems.
This feature automatically restricts agent capabilities when untrusted content enters the context:
| 🚫 Unsafe Agent | 🟢 Safe Agent with Dynamic Tools | 🟢 Safe Read-Only Agent |
|---|---|---|
| ✅ Can access private data | ✅ Can access private data | ✅ Can access private data |
| ✅ Can process untrusted content | ✅ Can process untrusted content | ✅ Can process untrusted content |
| ✅ Can communicate externally | 🤖 External communication dynamically disabled after processing untrusted data | 🚫 Cannot communicate externally |
Detect tools
The first step is to configure Archestra as a proxy for your agent's API requests. When your agent executes requests through the Archestra proxy endpoint, the platform automatically discovers and registers any tools included in those requests.
Tool discovery happens transparently:
- Configure your agent to send requests through Archestra's proxy
- When your agent makes API calls with tools, Archestra automatically detects them
- Each tool's name, parameters, and description are extracted and stored
- No manual tool registration or configuration required
This dynamic discovery allows Archestra to monitor and control tool usage without pre-configuration.
Mark tools
Archestra uses Trusted Data Policies to identify which tool outputs should be considered safe. By default, all data is untrusted - only explicitly marked data becomes trusted.

When a tool returns data:
- Archestra evaluates the output against all trusted data policies
- If no policy matches, the data is marked as untrusted
- The chat context becomes "tainted" when untrusted data enters
- This taint status affects what tools can be invoked subsequently
Security enforcement flow:
- When a tool is invoked, Archestra checks if the chat context is tainted
- If tainted and no explicit allow policy exists, the tool is blocked
- The agent receives a refusal message explaining the security violation
- This prevents data exfiltration and unauthorized actions after processing untrusted content
This creates a dynamic security boundary - agents maintain full capabilities with trusted data but are automatically restricted when handling potentially malicious content.